Nmap is an incredibly useful tool, but it’s even more useful if you understand the results of an Nmap scan. After a scan is complete, Nmap will categorize each scanned port into one of six states; open, closed, filtered, open|filtered, closed|filtered, and unfiltered.
The use of the vertical bar (|) or “pipe” is used to denote the use of “or.” The vertical bar is often used in programming to designate a logical “or” operation, and Nmap has borrowed this nomenclature for use in its output.
Some scan methods can only identify if a port is open, closed, or filtered, while other scan types might only be able to identify filtered or unfiltered ports. Where applicable, we’ve specified the scan types that apply to the port dispositions.
Nmap Port Dispositions
open
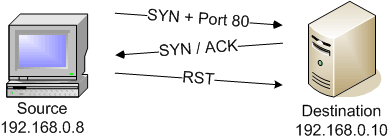
When Nmap interrogates a port and receives a positive response, the port is assigned the state of “open.” This is such a valuable state that Nmap even includes a special command line option, –open, to filter out all of the other port states. For example, Nmap’s TCP SYN scan (-sS) will receive a SYN/ACK from a remote device if a port is open:
# nmap 192.168.251.254 -p 25 Starting Nmap 4.20 ( http://insecure.org ) at 2007-02-27 16:47 Eastern Standard Time
Interesting ports on 192.168.251.254:
PORT STATE SERVICE
25/tcp open smtp
MAC Address: 00:50:E8:00:6A:D0 (Nomadix)
Nmap finished: 1 IP address (1 host up) scanned in 0.250 seconds
#
closed
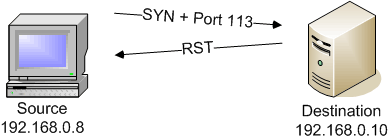
If Nmap determines that a port is not available, it assigns it the “closed” state. This signifies that Nmap has interrogated the port and has received a result that unequivocally shows that the port is closed. A TCP SYN scan (-sS) receiving a RST in response to a port query is an example of a closed port:
# nmap localhost -p 22,80Starting Nmap 4.20 ( http://insecure.org ) at 2007-02-27 17:33 EST
Interesting ports on localhost.localdomain (127.0.0.1):
PORT STATE SERVICE
22/tcp open ssh
80/tcp closed http
Nmap finished: 1 IP address (1 host up) scanned in 0.114 seconds
[root@localhost ~]#
filtered
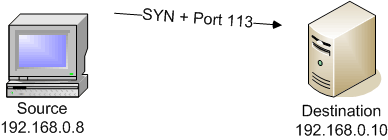
Filtered ports are the result of a packet filter or firewall. When no response at all is received from the remote device, the port is considered to be “filtered.” Since a response isn’t received from the port, Nmap often retries communication to the port to ensure that the packet wasn’t simply dropped due to error or congestion. Due to this retransmission process, filtered ports often cause delays during extensive Nmap scans.
This Nmap SYN scan sends a probe to a remote device, but a response is never received. Since this is a SYN scan, this response is categorized as “filtered.”
# nmap scanme.insecure.org -p80,8088
Starting Nmap 4.20 ( http://insecure.org ) at 2007-02-27 18:27 Eastern Standard Time
Interesting ports on scanme.nmap.org (205.217.153.62):
PORT STATE SERVICE
80/tcp open http 8088/tcp filtered unknown
Nmap finished: 1 IP address (1 host up) scanned in 6.656 seconds
open|filtered
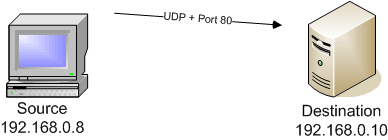
In some cases, the lack of a response may not necessarily mean that a port is filtered. In some cases, lack of a response might mean that the port might also be open. In these situations, Nmap signifies that the port is either filtered or open. The FIN scan (-sF), Xmas tree scan (-sX), Null scan (-sN) and UDP scan (-sU) can’t definitively determine an open port, so they always specify that the port is open|filtered.
# nmap -sU -v 192.168.0.10
Starting nmap 3.81 ( http://www.insecure.org/nmap/ ) at 2005-04-11 12:44 EDT
Initiating UDP Scan against 192.168.0.10 [1478 ports] at 12:44
Discovered open port 2001/udp on 192.168.0.10
The UDP Scan took 1.47s to scan 1478 total ports.
Host 192.168.0.10 appears to be up … good.
Interesting ports on 192.168.0.10:
(The 1468 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
123/udp open|filtered ntp
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
1031/udp open|filtered iad2
1032/udp open|filtered iad3
1900/udp open|filtered UPnP
2001/udp open wizard
4500/udp open|filtered sae-urn
MAC Address: 00:30:48:11:AB:5A (Supermicro Computer)
Nmap finished: 1 IP address (1 host up) scanned in 2.241 seconds
Raw packets sent: 1489 (41.7KB) | Rcvd: 1470 (82.3KB)
#
closed|filtered
There’s only one scan that identifies ports as either closed or filtered. Nmap’s idlescan (-sI) operates by spoofing a zombie’s IP address and querying the IPID of the zombie to determine if a response was received. If the IPID increments, then the port is open.
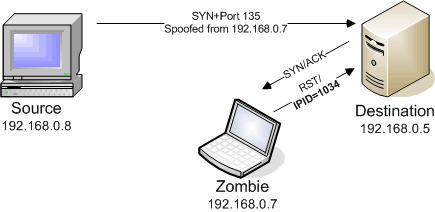
unfiltered
The TCP ACK scan (-sA) is often used to determine the availability of ports on a firewall or packet filter. The response to an out-of-sequence ACK will return a RST, which also signifies that the port is unfiltered.
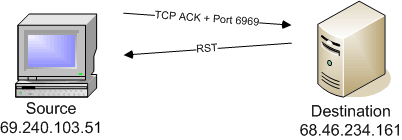
# nmap scanme.insecure.org -sA -p80,8088
Starting Nmap 4.20 ( http://insecure.org ) at 2007-02-27 19:40 Eastern Standard Time
Interesting ports on scanme.nmap.org (205.217.153.62):
PORT STATE SERVICE
80/tcp UNfiltered http
8088/tcp filtered unknown
Nmap finished: 1 IP address (1 host up) scanned in 6.484 seconds
#
Conclusion
Nmap is very descriptive in its port dispositions, so be sure to pay very close attention to the information in the output. When multiple scan methods are used on single scan, the results can be a mix of many different port designations.
