Increasing your Nmap Scanning Speed with –max-retries
If you’re scanning a filtered network, the Nmap option –max-retries can save time and bandwidth. The –max-retries option allows you to set the maximum number of retries that Nmap will attempt during a scanning session.
The practical use of this single option can be seen in this comparison. In this first example, the test server at insecure.org is scanned with only the -v (verbose) and -n (no reverse DNS lookup) options.
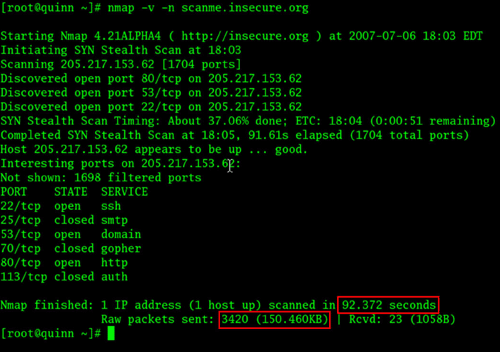
In the next example, I ran the same scan and added the additional option of –max-retries 0 on the Nmap command line. With this option, Nmap will never send a retransmission to a device that doesn’t answer the original port probe:
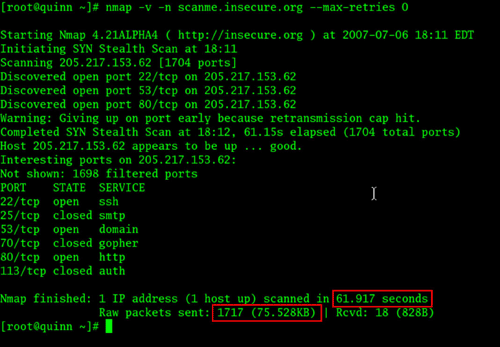
When to use –max-retries
If you’re on a network where filtering is slowing the scanning process, the –max-retries can be a useful supercharge to your scan. Nmap will still wait for a reply, but the number of retransmissions can be kept to a minimum.
If the network connectivity is questionable or dropped packets are normal (such as a wireless network), then the –max-retries option may cause Nmap to incorrectly identify ports as “filtered.” If you’re not sure, try enabling at least one retransmission to the target device.
