Although running Nmap with the default settings is very easy, it leaves an amazing amount of Nmap functionality unused. Nmap includes FIFTEEN different Nmap scan methods, and most people only use the default! There’s a lot of power just waiting to be tapped.
Although it’s useful to have fifteen different Nmap scan methods at your disposal, not all Nmap scans are interchangeable. At least one Nmap scan method rarely works on most modern networks, and another Nmap scan doesn’t actually scan anything!
The Nmap Scan
Once the Nmap ping process has completed (or been disabled with the -P0 option), the Nmap scanning process can begin. The default Nmap scan when running as a privileged user is the TCP SYN scan, and the default Nmap scan when operating as a non-privileged user is the TCP connect() scan. This graphic displays the process that occurs during a TCP connect() scan to an open port:
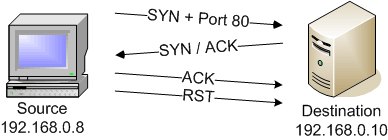
Both the TCP SYN scan and the TCP connect() scan are useful because they take advantage of the fundamentals of the TCP protocol. It would be unusual to find an instance where these scans wouldn’t work over non-filtered network connections.
Selecting an Nmap Scanning Method
Nmap provides a number of different scanning methods. Here.s a summary of all fifteen scanning types:
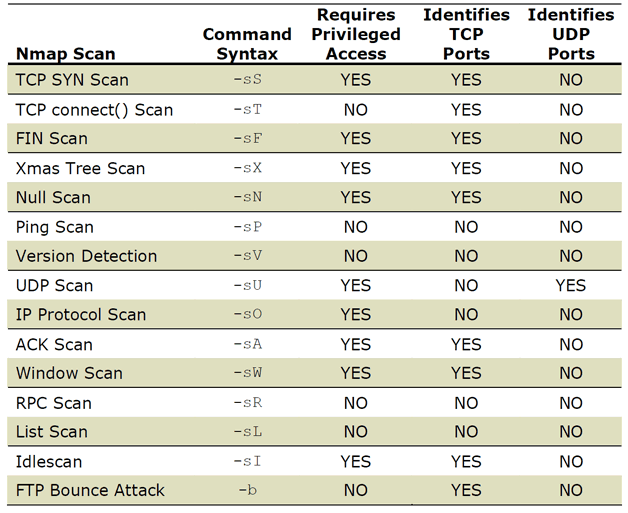
TCP SYN Scan (-sS) and TCP connect() Scan (-sT)
These are Nmap’s workhorse scans, and they’re the default scan methods because they can identify open TCP ports in almost any situation.
FIN Scan (-sF), Xmas Tree Scan (-sX) and Null Scan (-sN)
These three scanning methods are often called “stealth” scans because they send a single frame to a TCP port without any additional handshaking or additional data transfers. Although these are useful scanning methods, they will not identify ports when the target device is a Windows-based operating system.
Ping Scan (-sP)
The ping scan is one of the quickest scans that Nmap performs, since no actual ports are queried. Unlike a port scan where thousands of packets are transferred between two stations, a ping scan requires only two frames. This scan is useful for locating active devices or determining if ICMP is passing through a firewall.
Version Detection (-sV)
Most of Nmap’s scanning methods are based around the identification of port numbers. However, the version detection scan is most interested in the software applications running on a remote device.
UDP Scan (-sU)
The UDP scan is the only Nmap scanning method that identifies UDP ports. Open UDP ports are often overlooked, so the UDP scan may provide you with some important additional information about the remote device.
IP Protocol Scan (-sO)
The IP protocol scan is a bit different than the other Nmap scans. The IP protocol scan is searching for additional IP protocols in use by the remote station, such as ICMP, TCP, and UDP. If a router is scanned, additional IP protocols such as EGP or IGP may be identified.
ACK Scan (-sA)
Nmap’s unique ACK scan will never locate an open port. The ACK scan only provides a “filtered” or “unfiltered” disposition because it never connects to an application to confirm an “open” state. At face value this appears to be rather limiting, but in reality the ACK scan can characterize the ability of a packet to traverse firewalls or packet filtered links.
Window Scan (-sW)
The window scan uses the TCP sliding window values on certain operating systems to determine open TCP ports. This scan type does not refer to the operating system by a similar name.
RPC Scan (-sR)
The RPC scan is used in conjunction with another scanning method to identify remote procedure call-based applications running on a remote device.
List Scan (-sL)
The list scan is an Nmap scan that doesn’t actually scan any remote device, and it doesn’t send any packets across the network. This scan is often used as a “dry run” to test the parameters of an Nmap command line.
Idlescan (-sI)
Nmap’s idlescan is an ingenious method of indirectly scanning remote devices. Idlescan can also be used to identify the open TCP ports of devices that may reside on the other side of a firewall, even if the Nmap source station doesn’t have direct access to the target machine.
FTP Bounce Attack (-b)
The FTP bounce attack uses a standard, albeit unfortunate, technique in the ftp protocol to improperly transfer data to a third workstation. This technique is certainly a breach of security, and most FTP servers and security managers have modified their FTP servers to prevent this method from operating. In most modern networks, this scanning method is more of a technological study than a useful probe.
Choosing the Right Scan
Not all of Nmap’s scans are going to be applicable in every instance. Before running an Nmap scan, consider the goals of the scan and what you’d like to know when the scan completes. If you’re looking for an open UDP port, your only choice in a scanning method is the UDP scan (-sU). If you.re interested in identifying the filtered and unfiltered ports through firewalls, the TCP ACK scan (-sA) is often your best bet.
If you spend some time learning about these Nmap scanning methods, you’ll find your Nmap scans to be more effective and use fewer resources across your network.
