If you’ve ever run Nmap alone on the command line with simply a target IP address, then you’re probably using an inefficient method of performing your Nmap scans. Nmap includes many different command line options so you can tailor each scan to the results that you need.
In this article, we’ll learn more about optimizing Nmap pings to be the most efficient across your network. There are seven ping types to choose from, and you may be surprised to find that there’s an eighth option that could beat them all!
It’s easy to use Nmap to perform a security scan on a device, isn’t it? Here’s one of the simplest Nmap commands you’ll find:
#nmap 192.168.0.1
This scan is so simple that the only parameter on the Nmap command line is the IP address of the target device to be scanned. Unfortunately, this leaves a LOT of room for Nmap to make assumptions about what you want to accomplish during the scan.
The default Nmap scan chooses its own ping method, its own scanning method, and Nmap decides the ports that it will use during the scan. Over the next few Nmap mini-course lessons, we’ll look at various methods to make your Nmap scans more efficient every step along the way. In this lesson, we’ll focus on the Nmap ping process.
The Nmap Ping
Before Nmap will scan a device, it checks to be sure the device is really on the network. If the scan is to a local device, then Nmap performs a simple ARP to the device to determine if it’s alive. If the target station is on a different subnet, then Nmap uses a combination of an ICMP echo request and an out-of-order TCP ACK:
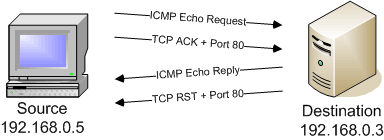
It’s important to note that the definition of an Nmap ping is different than the traditional ICMP ping command. Nmap can send various kinds of frames to a remote device to entice the device into responding, not just ICMP frames. Nmap isn’t necessarily looking for a positive or negative response; it just wants to get some type of frame in return.
The default ping is well suited as a default, but it may not be the most efficient. For example, the path to a remote device may filter ICMP well before it reaches the end station. In most cases, it’s the TCP ACK portion of the default ping that usually entices a response. In these situations, a more efficient Nmap scan would include the TCP ACK ping (-PA) option only. This new Nmap scan would be:
#nmap -PA 192.168.0.1
An even more efficient Nmap ping method may be to avoid pinging the remote device entirely! Nmap’s -P0 option disables Nmap’s ping process and forces Nmap to jump straight to the scanning process. If the ping is disabled and the device is on the network, then avoiding the ping process provides a more efficient Nmap scan without sacrificing any functionality.
However, this option isn’t appropriate in every circumstance. The problems begin to occur if an Nmap ping to a remote device is disabled and the remote IP address isn’t on the network. Once Nmap begins querying the ports of a remote device that isn’t really there, Nmap will have no choice but to retransmit every unanswered probe and the resulting Nmap scan becomes a very slow process.
Picking Pings
Nmap has a plethora of pings from which to pick. Here’s the entire list:
ARP Ping (-PR)
The ARP ping sends an Address Resolution Protocol packet to a device on a local subnet. Because this isn’t an IP frame, this ping can’t be used to identify devices across IP subnets.
ICMP Echo Request Ping (-PE)
This ping is a “real” ping, because it sends an ICMP echo request and looks for an ICMP echo reply. Since most smart firewalls are blocking ICMP, this option isn’t very useful to other protected networks.
TCP ACK Ping (-PA)
When the default Nmap ping works, it’s because the TCP ACK ping got a response. The ACK ping sends a random TCP ACK on port 80 to another device, and the out-of-order ACK usually prompts a response.
TCP SYN Ping (-PS)
The TCP SYN ping performs the same function as Nmap’s TCP SYN scan, but only uses a single port. Port 80 is used by default, but any port can be specified to assist with those hard-to-ping devices.
UDP Ping (-PU)
Don’t forget about UDP! With this ping type, you want to choose a port that ISN’T open, because a closed UDP port will usually reply with an ICMP port unreachable message. Of course, a protected network is probably filtering ICMP, so use this ping with the understanding that it may not always be the best choice.
ICMP Timestamp Ping (-PP)
The ICMP timestamp ping uses the “get timestamp” function of ICMP. This function is useful, but it still relies on ICMP to get the message from one side to another. Avoid this ping across filtered links.
ICMP Address Mask Ping (-PM)
The ICMP address mask ping is an unusual ICMP function, and most devices don’t give up critical information such as subnet masks. Again, the limitations of an ICMP-based ping still apply.
Some of these pings may be more appropriate than others, depending on what you’re trying to identify on the remote device. For example, if your Nmap scan is focused on identifying UDP ports it may be more appropriate to ping the remote device with a UDP ping.
Other Nmap pings might be useful in rare circumstances. For example, the ICMP address mask ping is an unusual method to use as an Nmap ping, but it can be relatively useful for identifying older systems that may respond to this antiquated ICMP method.
