Nmap is one of the best port scanners in the world, but did you know that Nmap can tell you the exact application name and version number hiding behind each port? More importantly, Nmap can tell you about the applications that you DON’T want to see! Nmap’s version detection capabilities can provide you with an easy method of identifying rogue devices.
What is Version Detection?
Nmap’s version detection feature identifies applications by performing intelligent queries of open ports. Even if the application is using a non-standard port, Nmap will correctly determine the application type.
Nmap uses a huge database of applications contained in the service file nmap-service-probes. This is constantly growing, so you may find additional services identified as time goes on. If you’ve found a new application, you will be given instructions on how to contribute your discovery to the next Nmap version!
How Version Detection Works
Version detection works by sending a series of queries to a port to determine the application type on the other side. For example, if Nmap queries a device on port 80, it will begin the version detection process with the most likely candidates:
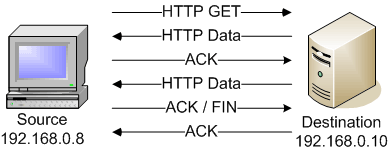
If the application running on port 80 is not a web service, Nmap will then begin querying for the next likely application type until it finds a suitable match.
Version Detection Prerequisites
Before a version scan can begin, it must be aware of which ports are open on a remote device. If a suitable scanning method is not specified on the command line, Nmap will select the default SYN scan if running as a privileged user, or a TCP connect() scan if running in non-privileged mode.
Once the scan is complete, the Nmap version detection process can begin. Nmap will begin scanning all services normally identified with the open port number before moving to other services with appropriate rarity values (more on rarity values later).
Here is the output from a typical version detection:
# nmap -sV 192.168.0.1 -v
Starting Nmap 4.20 ( http://insecure.org ) at 2007-03-22 23:21 Eastern Daylight Time
Initiating ARP Ping Scan at 23:21
Scanning 192.168.0.1 [1 port]
Completed ARP Ping Scan at 23:21, 0.11s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:21
Completed Parallel DNS resolution of 1 host. at 23:21, 4.61s elapsed
Initiating SYN Stealth Scan at 23:21
Scanning 192.168.0.1 [1697 ports]
Discovered open port 80/tcp on 192.168.0.1
Completed SYN Stealth Scan at 23:21, 1.02s elapsed (1697 total ports)
Initiating Service scan at 23:21
Scanning 1 service on 192.168.0.1
Completed Service scan at 23:21, 6.08s elapsed (1 service on 1 host)
Host 192.168.0.1 appears to be up ... good.
Interesting ports on 192.168.0.1:
Not shown: 1696 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Netgear WGR614v4 router http config (IP_SHARER WEB httpd 1.0)
MAC Address: 00:09:5B:D4:BB:FE (Netgear)
Service Info: Device: router
Service detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 12.046 seconds
Raw packets sent: 1698 (74.710KB) | Rcvd: 1699 (78.150KB)
TIP: Always run your Nmap scans with a verbosity level! There’s useful information printed to your screen that you’ll never see without using the verbosity output. Nmap uses levels of verbosity to determine how much information gets printed. A verbosity level of one is designated with -v, a verbosity level of two is -vv, and a verbosity level of three is -vvv.
Finding Rogue Devices
To locate rogue devices, your Nmap scan can be much more focused. If a rogue device is using a particular port number, it makes the scanning process much easier. In our example, let’s assume that we’re looking for rogue web servers in our organization that might be using port 80, port 8080, or port 8088. Our Nmap scan would use these command line options:
# nmap 192.168.0.* -p 80,8080,8088 -sV -vv
This will run a default TCP SYN scan to all IP addresses in the range 192.168.0.0 through 192.168.0.254 (192.168.0.*), but only ports 80, 8080, and 8088 will be scanned (-p 80,8080,8088). If any open ports are identified, Nmap will also perform a version scan (-sV) and the output from the scan will show all text at a verbosity level of two (-vv).
Other Version Detection Options
There may be situations where a version detection scan will need to run with minimal version checking, or perhaps you will require Nmap to check every service in the database to ensure that a match is found. In these situations, Nmap’s “rarity” feature will become very useful.
Every service in Nmap’s nmap-service-probes file is assigned a rarity value based on a relative determination when it’s added to the database. Rarity values can be assigned a number between 1 (very common) to 9 (very rare). To manually assign a rarity, the command line option –version-intensity can be used with the appropriate rarity value.
Nmap also includes rarity shortcut command. Using the option –version-light will set the rarity value to 2, and –version-all does exactly what it sounds like by setting the rarity value to 9.
A relatively new “feature” in the version detection process is the exclusion of port 9100. If this port is identified as open, Nmap will not perform a version scan on the port unless the option –allports is used on the command line. This is because port 9100 is often associated with print servers and previous Nmap version detection scans would result in unintended printing!
